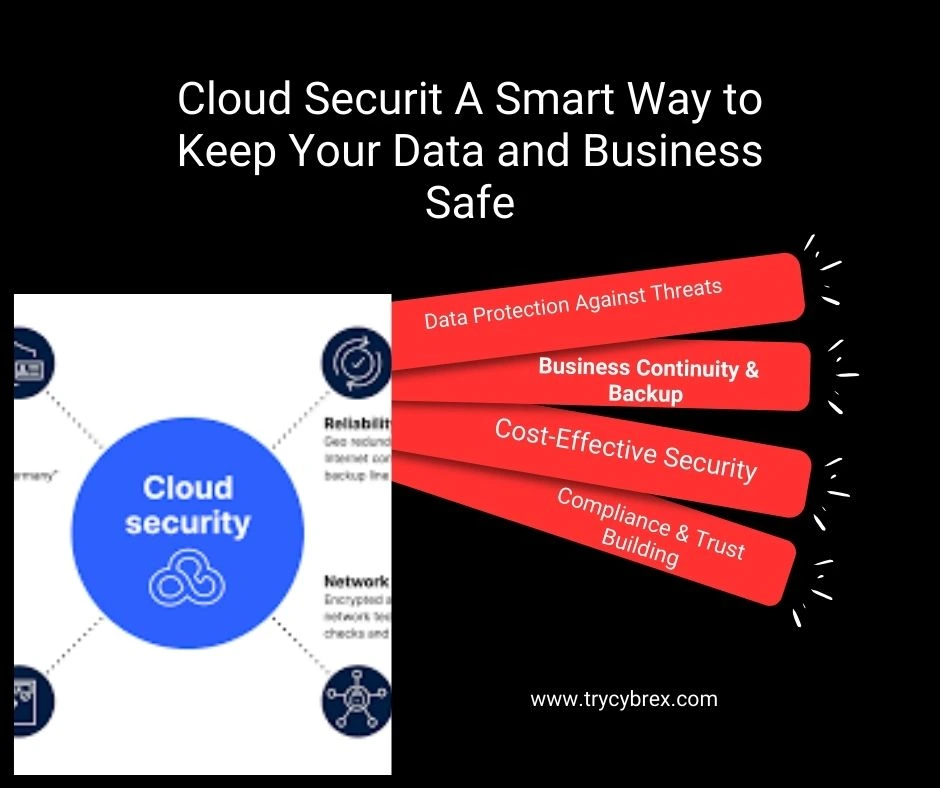
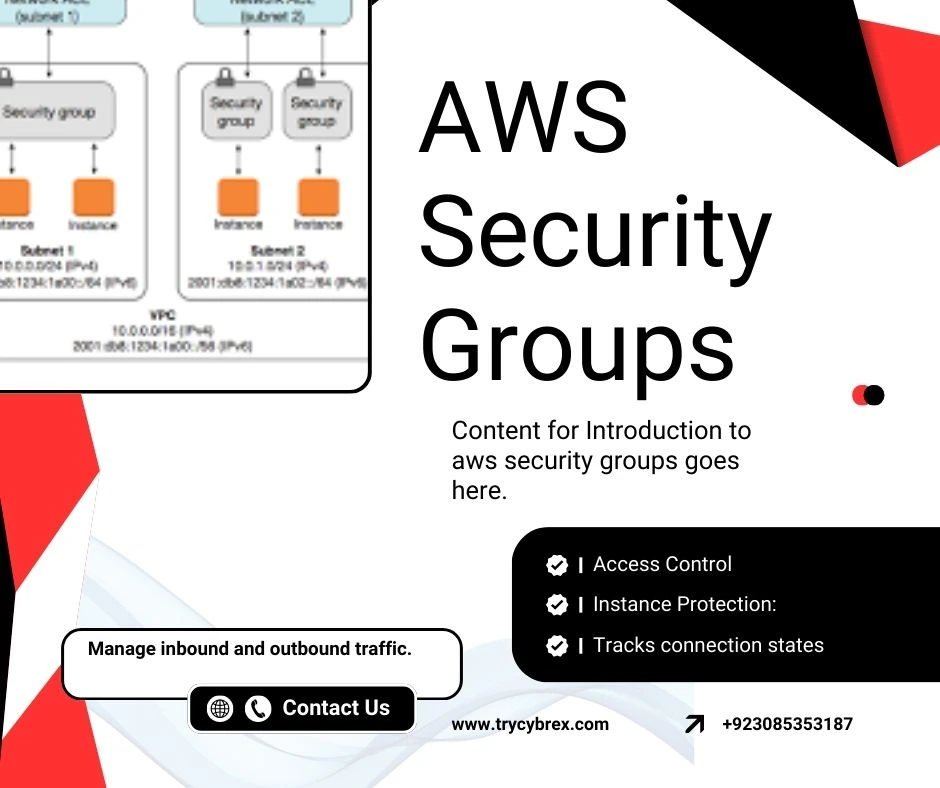
Content for Introduction to AWS CloudTrail goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘introduction to AWS CloudTrail and Virtual Private Cloud (VPC)’ in the context of AWS management and security.
Why CloudTrail is Essential
Content for Why it is Essential goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘why it is essential’ in the context of AWS management, security, and Threat Hunting.
Setting Up CloudTrail
Content for Setting Up goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘setting up it’ in the context of AWS management, security, and EDR Cyber Security.

Analyzing CloudTrail Logs
Content for Analyzing AWS CloudTrail Logs goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘analyzing logs’ in the context of AWS management and security.
Integrating with AWS CloudWatch
Content for Integrating with AWS CloudWatch goes here. This section will cover in-depth details, best practices, examples, and actionable insights about integrating with AWS CloudWatch in the context of AWS management and security. It will also highlight how AWS CloudWatch helps in monitoring and responding to a security breach, ensuring that potential vulnerabilities are detected and addressed proactively to maintain a secure environment.
Automating Security Alerts
Content for Automating Security Alerts goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘automating security alerts’ in the context of AWS management and security.if you more read relvent post then click this post link How to Secure Your AWS Environment with IAM Policies

Best Practices for CloudTrail Management
Content for Best Practices for Management goes here. This section will cover in-depth details, best practices, examples, and actionable insights about best practices for its management in the context of AWS management and security, with a focus on information security. It will provide guidance on ensuring that AWS environments are secure and meet the highest standards of information security to protect sensitive data and systems.
Conclusion
Content for Conclusion goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘conclusion’ in the context of AWS management and security, with an emphasis on internet security. It will summarize how leveraging AWS tools and best practices enhances internet security by securing cloud-based environments and mitigating online threats.