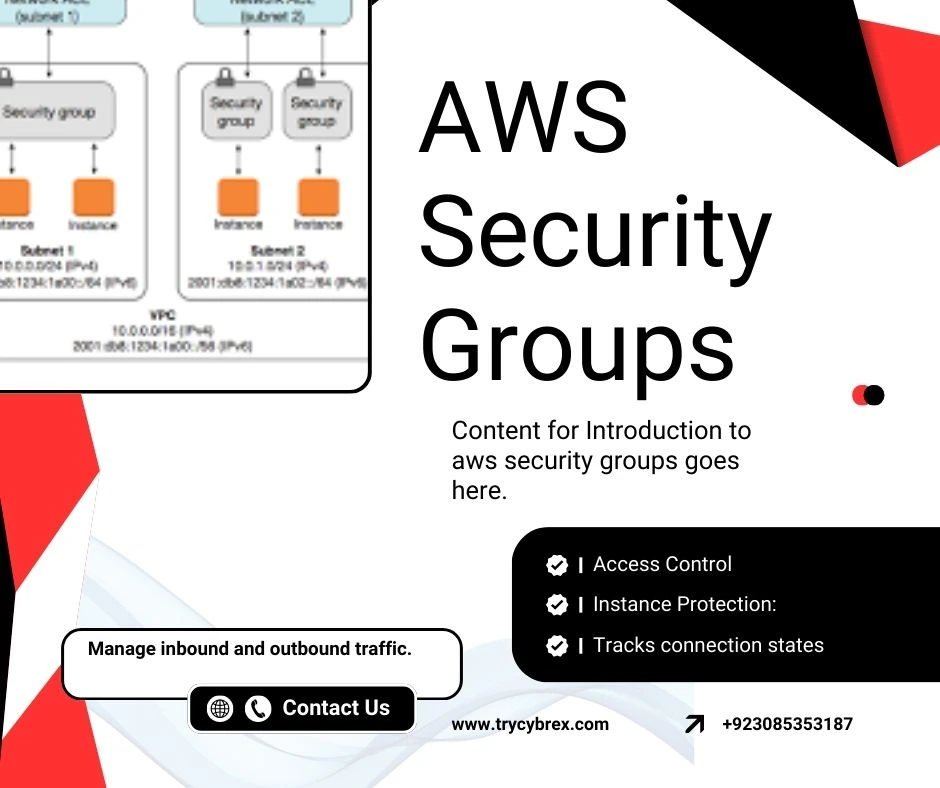
Content for Introduction to AWS security groups goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘introduction to AWS security groups,’ including the role of network firewalls in enhancing security within AWS environments.
Understanding AWS Security Groups
Content for Understanding Security Groups goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘understanding security groups’ in the context of AWS management and security.
How Network ACLs Work
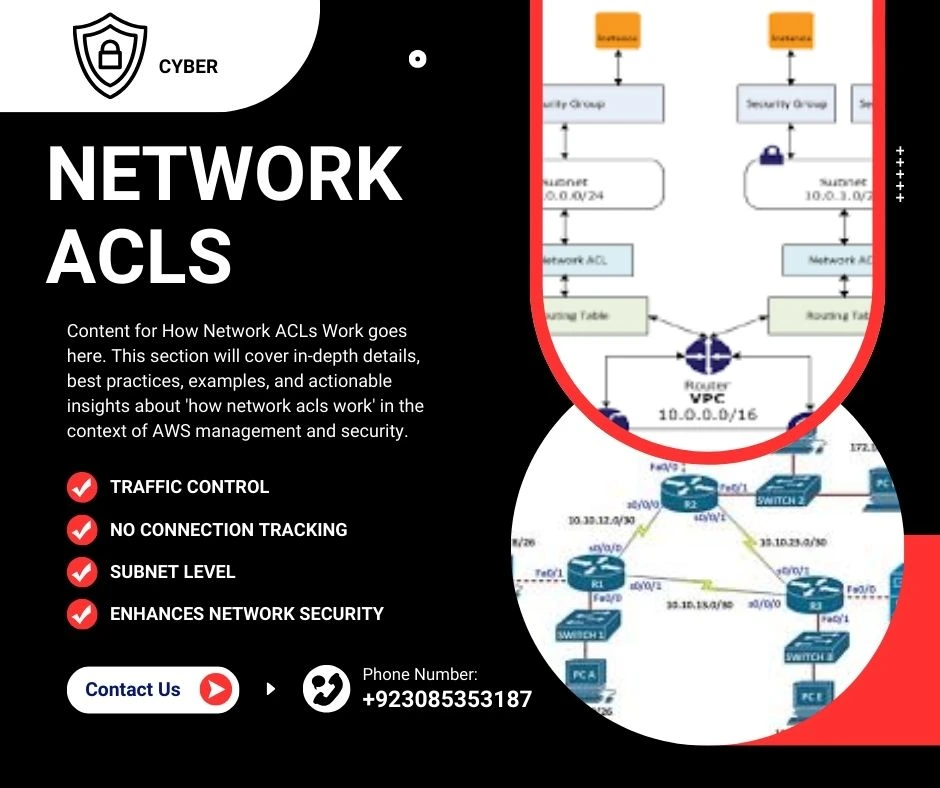
Content for How Network ACLs Work goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘how network ACLs work’ in the context of AWS VPC management and security.
Best Practices for Security Groups
Content for Best Practices for AWS security groups goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘best practices for security groups’ in the context of AWS management and security, including essential elements like malware protection and intrusion detection.
Configuring NACLs for Layered Security
Content for Configuring NACLs for Layered Security goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘configuring nacls for layered security’ in the context of AWS management and security. if you more read relevent post then cliuxk this link AWS Config Optimizing AWS Security with Automation and Insights
Common Mistakes and How to Avoid Them
Content for Common Mistakes and How to Avoid Them goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘common mistakes and how to avoid them’ in the context of AWS management and security, with a focus on ensuring secure access to AWS resources.

Monitoring Network Traffic
Content for Monitoring Network Traffic goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘monitoring network traffic’ in the context of AWS management and security, including the role of penetration testing in identifying vulnerabilities
Conclusion
Content for Conclusion goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘conclusion’ in the context of AWS management and security.