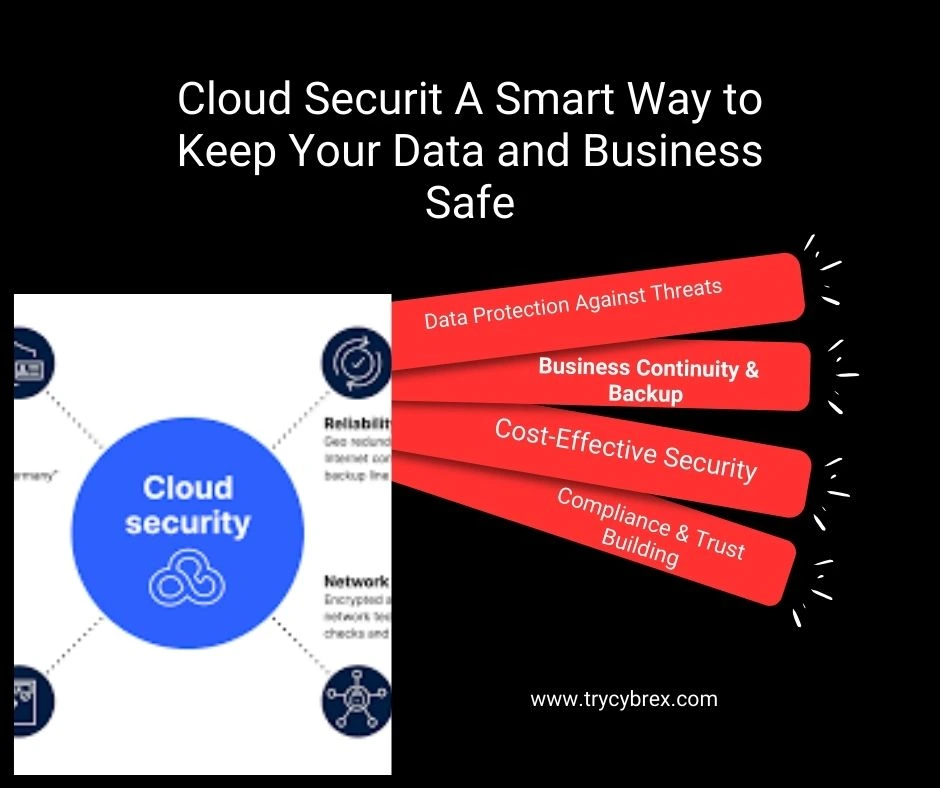
AWS Management & Security goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘introduction to aws management & aws security in the context of AWS management and security, with practical references to the AWS Management Console for better understanding and implementation.
Why AWS Security is Critical
Content for Why AWS Security is Critical goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘why aws security is critical’ in the context of AWS management and security, with relevant considerations of how the AWS Console supports secure configurations and monitoring.
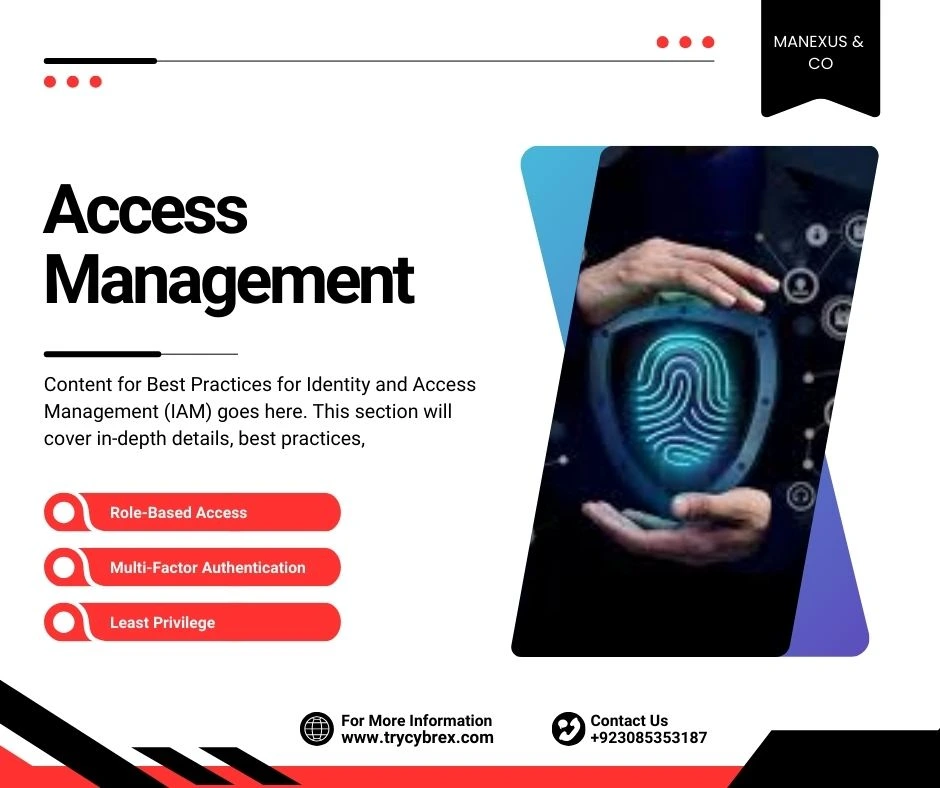
Best Practices for Identity and Access Management (IAM)
Content for Best Practices for Identity and Access Management (IAM) goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘best practices for identity and access management (iam)’ in the context of AWS management and security, with practical applications across different AWS Services.
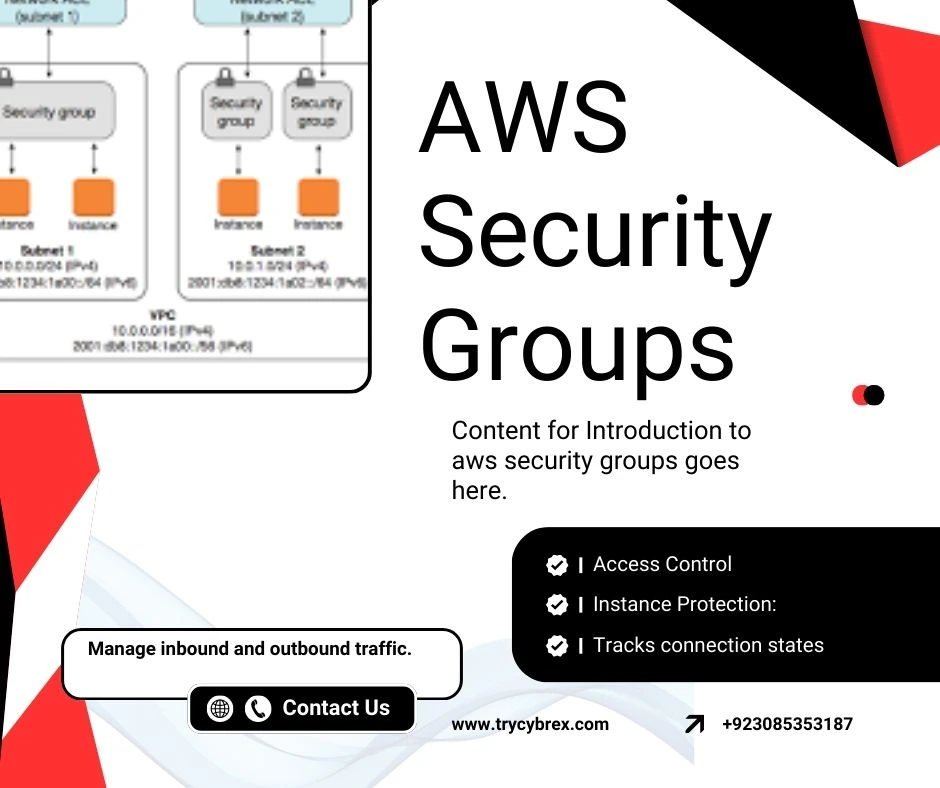
Implementing Network Security in AWS
Content for Implementing Network Security in AWS goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘implementing network security in aws’ in the context of AWS management and security, with a focus on securing workloads and resources within the AWS Cloud.
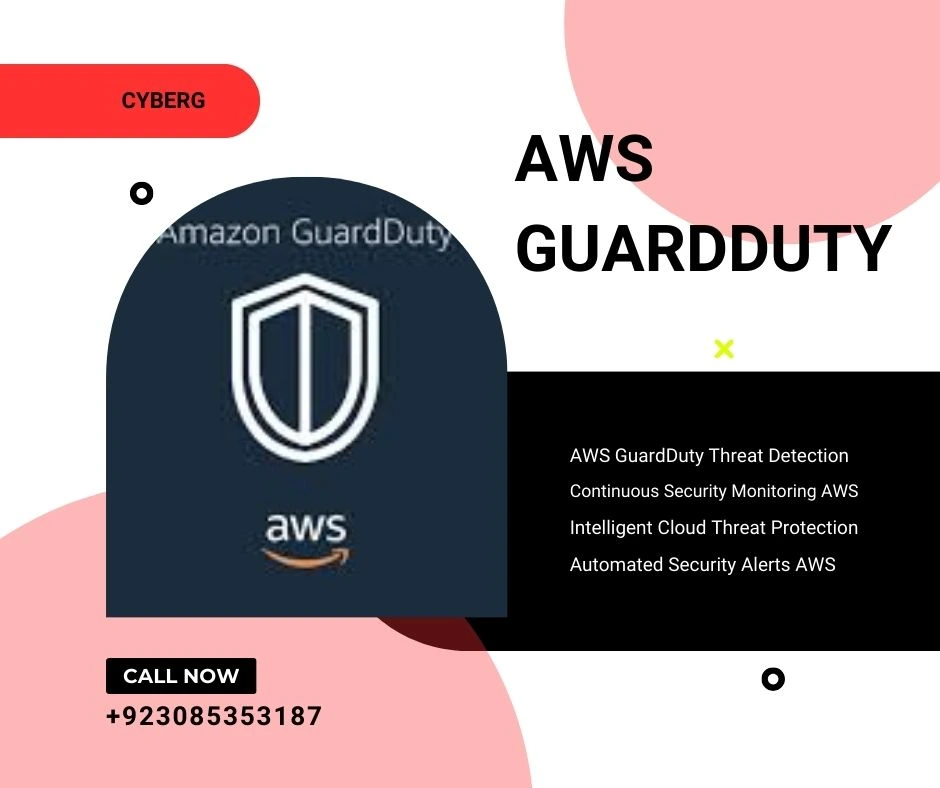
Monitoring and Logging for Security
Content for Monitoring and Logging for Security goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘monitoring and logging for security’ in the context of AWS management and security, highlighting how AWS Support can assist in maintaining and troubleshooting these security processes. if you more read relvent post then click this link The Role of Ethical Hacking in Website Security: How Pen Testing Protects Your Business/
Data Encryption and Key Management
Content for Data Encryption and Key Management goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘data encryption and key management’ in the context of AWS management and security, including how AWS CloudWatch can be used to monitor encryption processes and key management activities.
Incident Response Strategies in AWS
Content for Incident Response Strategies in AWS goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘incident response strategies in aws’ in the context of AWS management and security.
Conclusion
Content for Conclusion goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘conclusion’ in the context of AWS management and security.