Content for Introduction goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘introduction’ in the context of AWS management, AWS security groups, and common AWS Misconfigurations.
Understanding AWS Misconfigurations
Content for Understanding AWS Misconfigurations goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘understanding aws misconfigurations’ in the context of AWS management, Cloud Security, and overall AWS security.
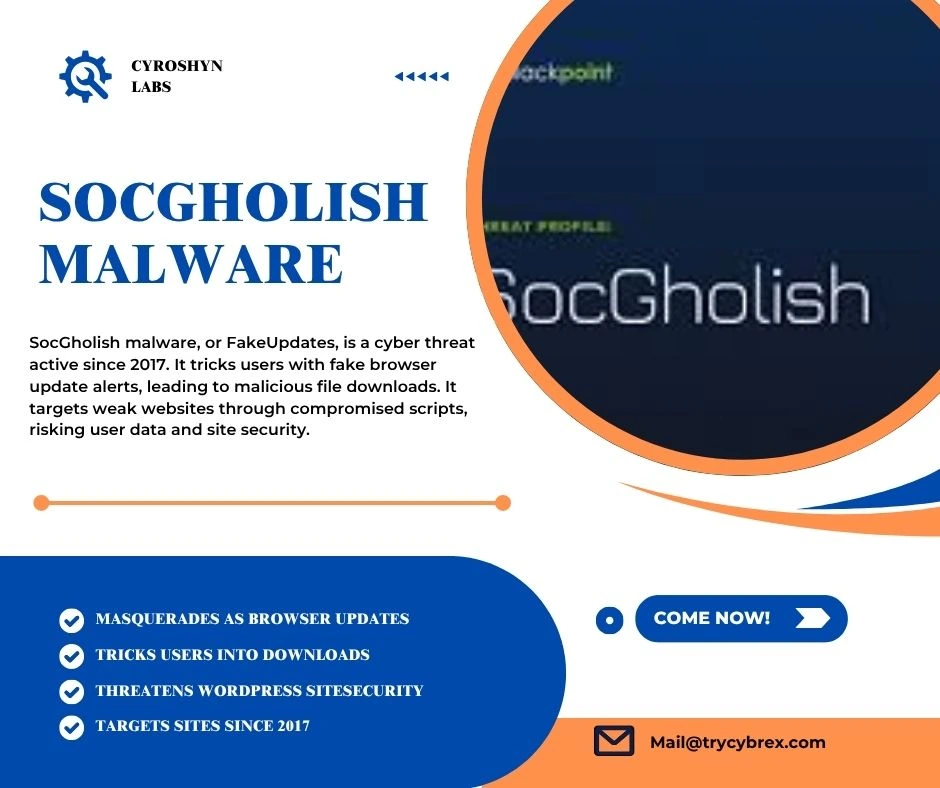
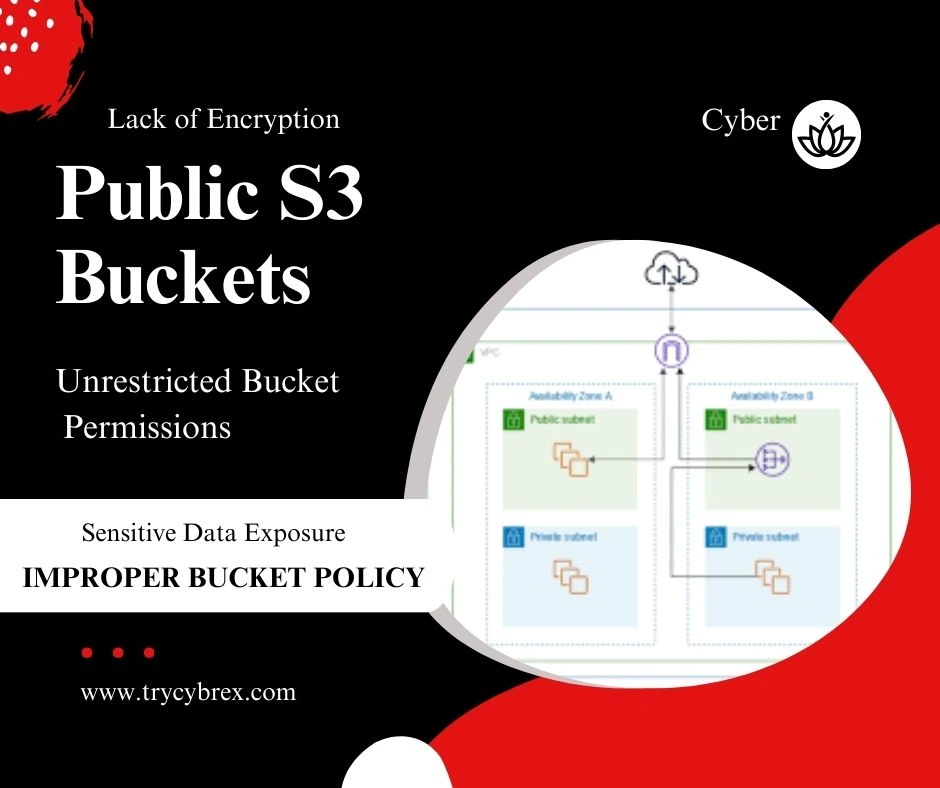
Public S3 Buckets
Content for Public S3 Buckets goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘public s3 buckets’ in the context of AWS management, AWS IAM, and security.
Over-Permissive IAM Roles
Content for Over-Permissive IAM Roles goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘over-permissive iam roles’ in the context of AWS management and security.
Unrestricted Security Groups
Content for Unrestricted Security Groups goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘unrestricted security groups’ in the context of AWS management, AWS CloudTrail, and security.
Disabled CloudTrail Logging
Content for Disabled CloudTrail Logging goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘disabled cloudtrail logging’ in the context of AWS management and security. If you’re interested, read more relevant posts by clicking this link AWS Security and Management Comprehensive Guide to Best Practices.
Lack of MFA on Root Accounts
Content for Lack of MFA on Root Accounts goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘lack of mfa on root accounts’ in the context of AWS management, Multi-Factor Authentication, and security.
Unpatched EC2 Instances
Content for Unpatched EC2 Instances goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘unpatched ec2 instances’ in the context of AWS management, AWS GuardDuty, and security.
Improper Key Management
Content for Improper Key Management goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘improper key management’ in the context of AWS management, AWS Shield, and security.
Failure to Enable GuardDuty
Content for Failure to Enable GuardDuty goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘failure to enable guardduty’ in the context of AWS management, security, and DDoS Protection.
Conclusion
Content for Conclusion goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘conclusion’ in the context of AWS management, security, and AWS WAF.