“Content for Introduction to AWS Config goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘introduction to AWS Config’ in the context of AWS management and security, with a special focus on incident response automation. Learn how AWS Config can streamline incident response automation, ensuring faster and more efficient handling of security incidents while maintaining full compliance with industry best practices.”
Why AWS Config is Important
“This section will cover in-depth details, best practices, examples, and actionable insights about ‘why AWS Config is crucial’ in the context of cloud management, security, and infrastructure optimization. Discover how AWS Config helps manage and secure cloud infrastructure, ensuring compliance and enhancing operational efficiency.”
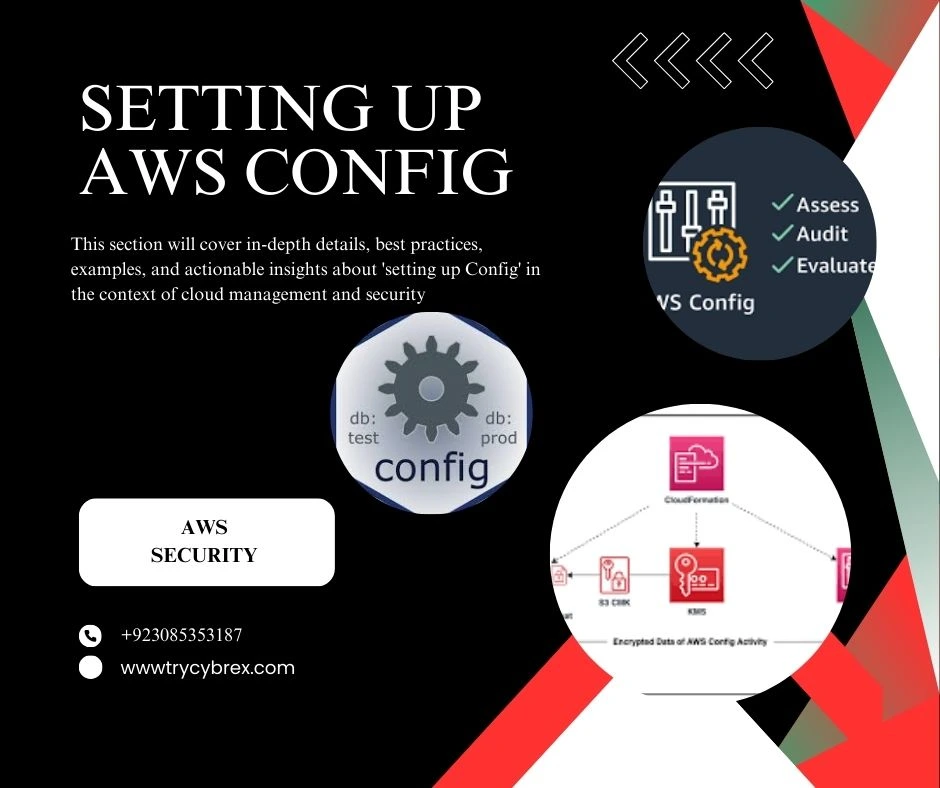
Setting Up AWS Config
“This section will cover in-depth details, best practices, examples, and actionable insights about ‘setting up Config’ in the context of cloud management, security, and industrial automation. Learn how AWS Config can help streamline processes, enhance compliance, and integrate seamlessly with industrial automation systems for better efficiency and control.”
Creating Custom Config Rules
Content for Creating Custom Config Rules goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘creating custom config rules’ in the context of AWS management and security.
Auditing AWS Resources
“Content for Auditing AWS Resources goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘auditing AWS resources’ in the context of AWS management and security, with a focus on Test Automation and Automation Software. Learn how these tools can enhance the efficiency and accuracy of auditing processes, ensuring better security and compliance across your AWS resources.”
Remediating Non-Compliant Resources
“Content for Remediating Non-Compliant Resources goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘remediating non-compliant resources’ in the context of AWS management and security, with a focus on Data Automation. if you more read relvent post then click this link AWS GuardDuty Proactive Threat Detection in the Cloud
Best Practices for AWS Config
This section will cover in-depth details, best practices, examples, and actionable insights about ‘best practices for Config’ in the context of cloud management and security.
Conclusion
Content for Conclusion goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘conclusion’ in the context of AWS management and security.