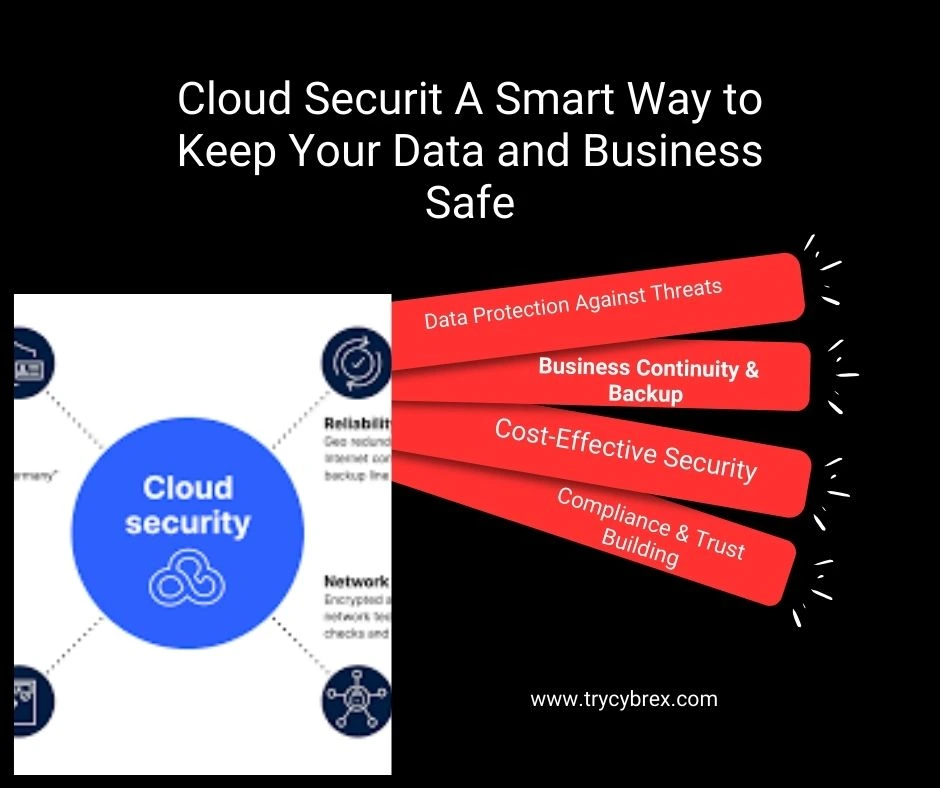
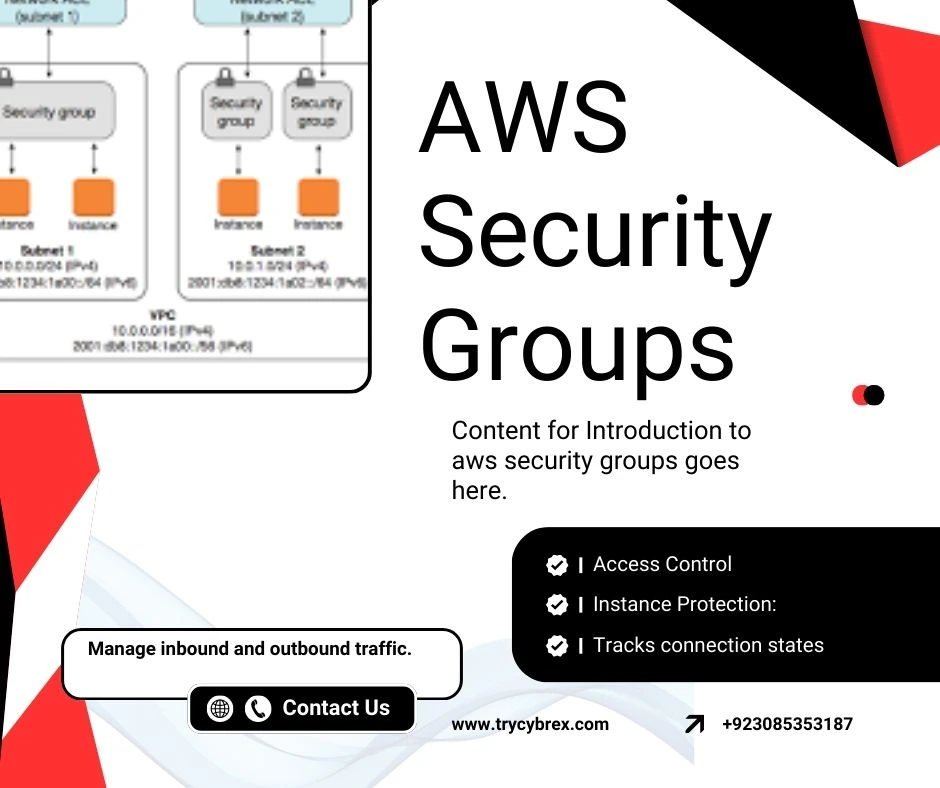
Content for Introduction to AWS Data Encryption goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘introduction to AWS data encryption’ in the context of AWS management and security. It will also highlight how data encryption helps protect against potential insider threats by ensuring that sensitive data remains secure even when accessed by authorized users.
Data at Rest Encryption Options
Content for Data at Rest Encryption Options goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘data at rest encryption options’ in the context of AWS management and security. It will also explain how effective security management practices, including the integration of SIEM systems, enhance the protection of data at rest by providing real-time monitoring and threat detection.
Data in Transit Encryption Options
Content for Data in Transit Encryption Options goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘data in transit encryption options’ in the context of AWS management and security.
Using AWS KMS for Key Management
Content for Using AWS KMS for Key Management goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘using aws kms for key management’ in the context of AWS management and security. if you more rea relvent post then click this link AWS CloudTrail The Cornerstone of Security Monitoring.
Integrating Data Encryption into Applications
Content for Integrating Data Encryption into Applications goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘integrating data encryption into applications’ in the context of AWS management and security. It will explain how implementing data encryption ensures secure data transmission and storage, safeguarding sensitive information from potential threats, while supporting digital forensics investigations and aligning with a zero trust security model to ensure only authorized access to data.
Best Practices for AWS Encryption
Content for Best Practices for AWS Encryption goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘best practices for AWS encryption’ in the context of AWS management and security. It will explain how implementing strong encryption practices helps protect sensitive data from potential threats, including ransomware attacks, ensuring that data remains secure and recoverable.

Auditing and Compliance
Content for Auditing and Compliance goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘auditing and compliance’ in the context of AWS management and security. It will also emphasize the importance of encryption as a critical component in ensuring data protection and compliance with industry regulations during the auditing process.
Conclusion
Content for Conclusion goes here. This section will cover in-depth details, best practices, examples, and actionable insights about ‘conclusion’ in the context of AWS management and security. It will also highlight how security software plays a crucial role in complementing AWS security practices, ensuring that sensitive data remains protected and resilient against potential threats.